Prerequisites – The user of this post is expected to have some knowledge on
- What the Nexpose tool does?
- Where it is applicable?
This post is aimed at familiarizing the user with the practical usage of the tool. However we will have a quick look at the architecture of Nexpose.
Nexpose Components
- Nexpose Security Console
- Nexpose Scan Engine
- Nexpose Database
- Java Expert System Shell
- Nexpose API
Nexpose Security Console (NSC): NSC is basically the web console through which you can manage your assets, configure and schedule scans, make reports, administration and user management. Accessible by port 3780 by default, but changeable.
Usage : https://[Server IP]:3780/
 The screenshot above shows the login screen of NSC. After you login you will get something like below
The screenshot above shows the login screen of NSC. After you login you will get something like below

You can see tabs like Assets, Vulnerabilities, Policies, Reports and Administration on top. Assets are basically the devices that need to be scanned. Every asset is identified by its IP address. Clicking on the ‘Vulnerabilities’ tab gives you all the vulnerabilities that were identified on the assets. We will discuss in detail about the tabs as we progress.
Nexpose Scan Engine (NSE): This is basically the workhorse in Nexpose. This module is responsible for running scans against assets. All communication between NSE and NSC occurs via encrypted SSL sessions. NSC controls scan configuration and scheduling. Updates are pushed from NSC to NSE. NSE basically runs as a service at port 40814 on the server (NSE can be on the same machine where NSC resides or on a different one).
Nexpose Database: Nexpose uses ‘PostgreSQL 9.1.x’ database. It is usually integrated with the console. However no direct access to the database is provided.
Java Expert System (JESS): This module adds to the intelligence of NSE. It continuously feeds newly discovered information back into the program to dig deeper and identify more vulnerabilities, which further improves the efficiency during the scan process. This also reduces false positives/adverse effects.
Nexpose API: There are two versions for the API. API 1.1/1.2 . The API uses HTTP protocol over SSL, which makes it easy to be integrated in to other applications. Data is transported using XML.
Simple scan using Nexpose (target – Linux box):
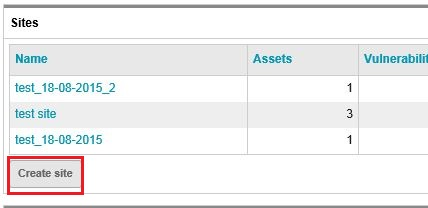
Log in to your Nexpose Security console with valid credentials. At the home page of the console, scroll down and come to the ‘Sites’ table. Click on ‘Create site’.
Before you could scan any asset in Nexpose, a site has to be created. A site basically contains
- Scan target(s) (or assets)
- Scan template
- Scan Engine (NSE’s)
- Scan Schedule (optional)
- Alerts (optional)
- Credentials (optional)
After you click ‘Create site’, you will land on a page as shown below.

First you have to provide a name for the site. Let it be ‘myfirst_scan’ as for now. When the green tick appears near the name, you are good to go. Now click on the ‘ASSETS’ tab. Here you will have to provide the IP addresses of the assets you want to scan. You can either provide a subnet using the CIDR form (eg: 10.0.0.8/24), provide IP address ranges (eg: 10.0.0.8 – 10.0.0.56) or provide each IP address separated by comma. As of now I have a single asset, which is a metasploitable Linux at 10.179.21.85 (This is basically a virtual machine that has been set up in the cloud for demonstration purpose. You could download a copy of Metasploitable Linux from Metasploitable 2). You will have to just type the IP address of the asset in the field and press ‘Enter’ key. (NB: The IP address of the asset could be different for you)

As shown in figure above, the system has accepted the IP address we have provided. We will skip the ‘AUTHENTICATION’ tab for now. Click on the ‘TEMPLATES’ tab.

Here you see all of the available scan templates. We have Denial of service, Discovery scan, Discovery Scan – Aggressive, Exhaustive and so on. First let’s keep things simple. We will do a ‘Discovery Scan’. In discovery scan, it first gives out ICMP ping probes to check if the asset is alive or not (Uses TCP/UDP probes if ICMP is blocked). Secondly it does ‘Service Discovery’ (using TCP and UDP packets) to identify all the open ports and the services running on the ports. ‘Checks’ are being disabled, which means no vulnerability checks for now. Click on the ‘ENGINES’ tab now.

Choose ‘Local scan engine’ as of now. This is the workhorse for our scan. We have not created any ‘ALERTS’ for now, so we will just skip that as well. ‘SCHEDULE’ is only required if you want to schedule your scan for a later time. Now go ahead and click on ‘SAVE & SCAN’. The scan should start now. You should see a window like below that gives you the progress of the scan.

Once the scan gets completed, you will get to see a ‘Completed Successfully’ message under the ‘status’ for your scan. Also you will see the IP address(s) of your asset(s) under ‘Completed Assets’. See the screen below for reference

Now if you click on the IP address of your asset under ‘Completed Assets’, it will take you to a page that shows you the results of this particular scan for the asset. You can see that Nexpose has identified the OS to be Ubuntu Linux 8.04.

The ‘Vulnerabilities’ table seems empty, since we didn’t ask the tool to dig for vulnerabilities. Also there were no policies selected. But if you scroll down further, you will get to see the services the tool has identified along with the port numbers. As we have mentioned earlier, the purpose of a ‘Discovery Scan’ was to identify these services.

The tool identified that the machine at 10.179.21.85 has hosted FTP,SSH,Telnet,SMTP,HTTP and CIFS services. It was also able to identify the product versions in use for these services. Also the ‘Node Fingerprints’ are being listed out with the source that helped to identify each of them.